Consumer technology vendors often advise their customers to only install updates and patches only via the official channels to ensure that the integrity of the system is maintained. But what if your PC maker’s official update utility contains malware?
That’s exactly what has happened with about 1 million owners of Asus computers. First reported byMotherboard, the hackers were able toinfect the company’s serverand exploit it to distribute malware for at least five months.

Uncovered bythe Russian cybersecurity firm Kaspersky Labs, the backdoor was installed ona range of devices, including laptops, smartphones, smart home systems, desktop PCs, and other consumer electronics devices. Moreover, the firm has dubbed the attack asShadowHammer.
The hackers were able to make sure that the infected utility was signed using a legitimate certificate and they even made sure that the file size matched with the original update utility.
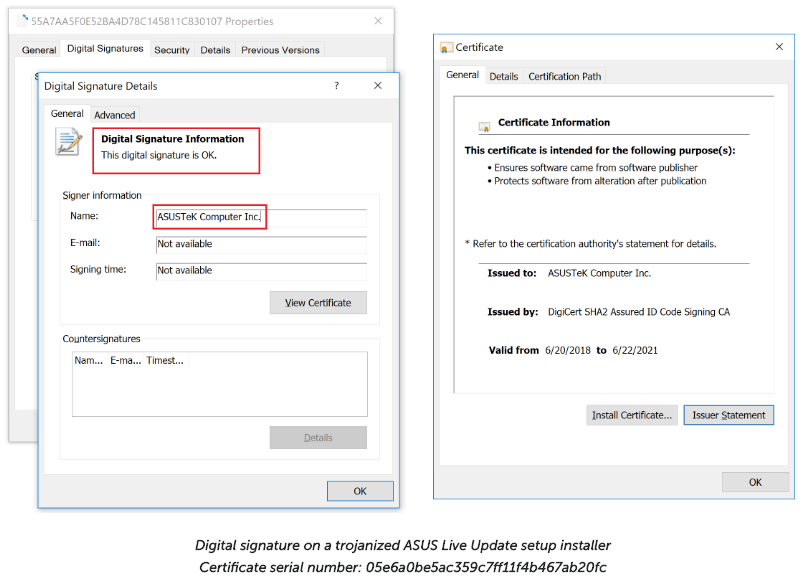
While Kaspersky has released some details of this “sophisticated supply chain attack,” the company plans to release a detailed analysis of this attack next month at its cybersecurity conference.
Even though the firm has mentioned the possibility of more than a million users being affected, it has yet to confirm the total count.
What makes this attack even more interesting is the fact that the attack was performed totarget a specific poolof users who were matched using their MAC addresses. The hackers embedded a list of addresses in the malware and used it to identify the target users.
The Asus users can either check their MAC addressesonlineor run thistoolto confirm if they are affected.